
The Need for Unified Observability for Modern Businesses
Gone are the days of monolithic applications and siloed data centres. Enterprises are increasingly adopting …
Hackers pose a persistent threat to businesses, devising new ways to steal data and disrupt operations. They exploit human vulnerabilities through phishing emails that mimic trusted sources, tricking employees and causing costly data breaches.
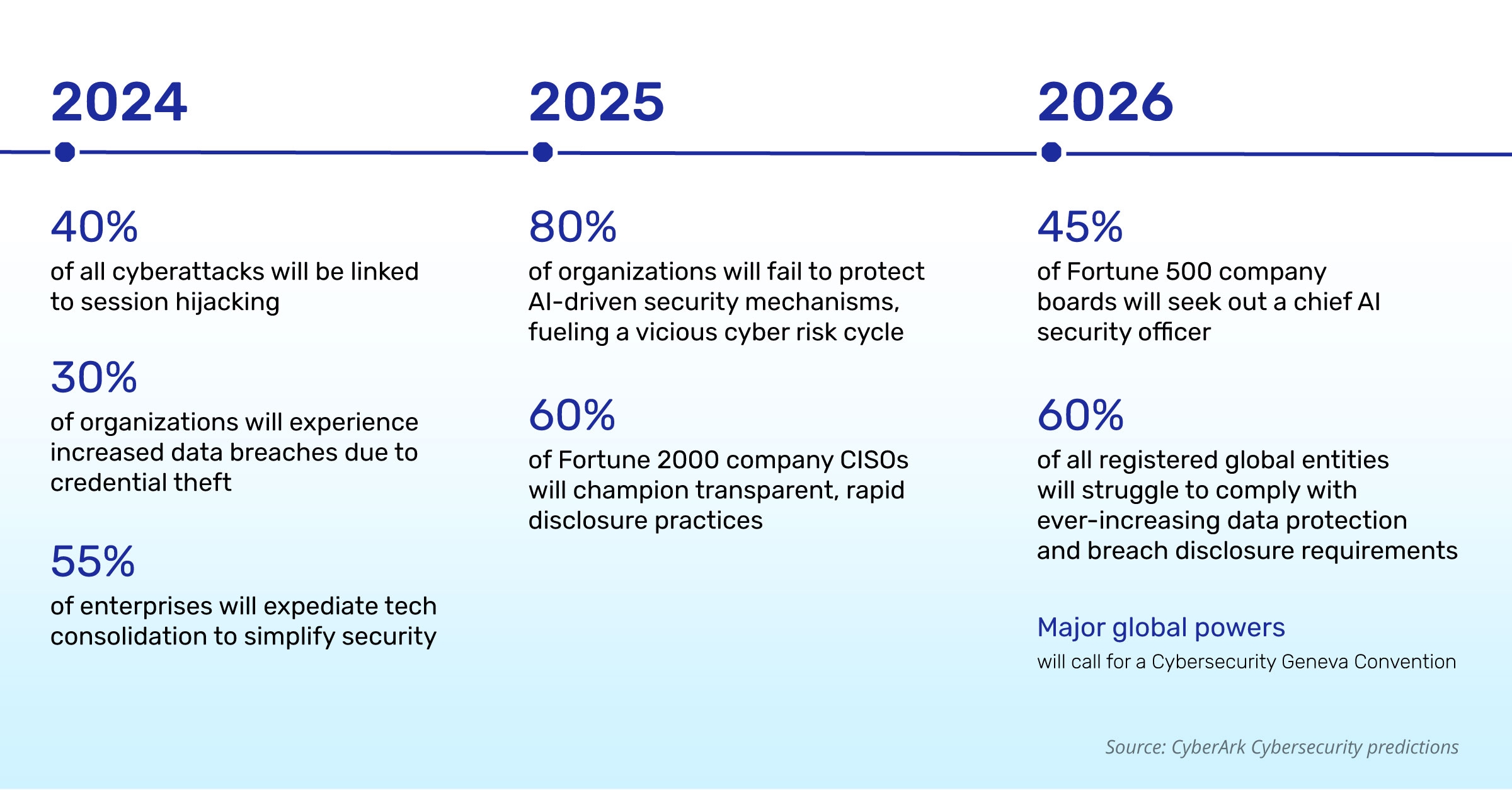
According to Forbes, global cybercrime damage costs are expected to reach $10.5 trillion annually by 2025, reflecting a 15 percent growth per year over the next two years. Considering the potential consequences, CEOs and executives need to prioritize cybersecurity and take steps to safeguard their systems from code exploits. There is an urgent need to adopt DevSecOps and integrate security into every stage of software development to protect against evolving cyber threats effectively.
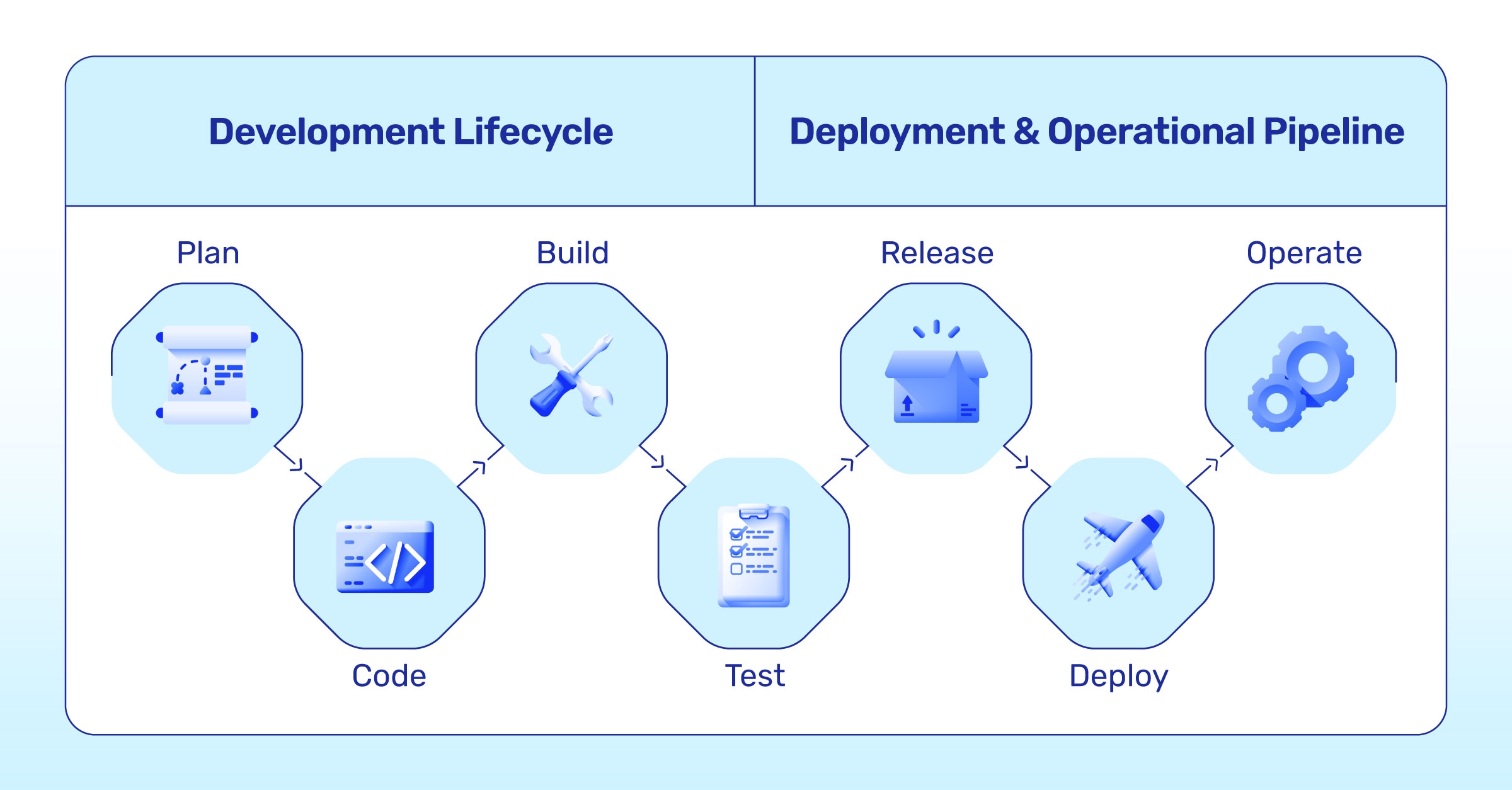
DevSecOps, short for development, security, and operations, is a software development approach that automates the integration of security practices at every stage of the software development lifecycle (SDLC). From initial design through integration, testing, delivery, and deployment, DevSecOps ensures security measures are seamlessly incorporated.
The main goal of DevSecOps is to integrate security into the fast-paced software release process, aiming to reduce the risk of security vulnerabilities and breaches in modern applications.
“Central for any executive is ROI and if a decision will bring their business forward or backward,” Ayoub Fandi, - Senior Field Security Engineer at GitLab
DevSecOps is all about making security an integral and ongoing part of the software development process, rather than treating it as an isolated, late-stage concern.
Although DevSecOps offers numerous benefits, adopting it can present considerable challenges for organizations, requiring substantial shifts in both mindset and processes.
Lack of Skill and Expertise: Effective DevSecOps implementation relies on knowledgeable personnel who understand security practices and automation tools. Organizations may need to invest in training or hire experienced professionals to bridge the skill gap.
Tool Selection: Choosing the right tools for security testing and automation is crucial. The vast array of available tools can be overwhelming, and selecting the best fit for an organization’s needs can be challenging.
Compliance and Regulation: Meeting industry-specific compliance requirements while adopting DevSecOps practices can be difficult. Organizations need to ensure that their security practices align with the relevant regulations, which may involve additional documentation and reporting.
Resource Constraints: Implementing DevSecOps can require a significant investment in terms of time and resources. Smaller organizations or teams with limited budgets may face constraints when trying to adopt comprehensive DevSecOps practices.
Legacy Systems: Adapting DevSecOps practices to legacy systems that were not originally designed with security in mind can be difficult. Integrating security into such systems may require significant effort. including refactoring code, updating dependencies, and implementing automated security testing.
DevSecOps works well when an organization uses Agile methods to quickly integrate, deploy, and scale their software. It might take some time to get everything working smoothly, but when done right, DevSecOps helps release products faster and at a lower cost. Plus, it helps ease concerns about coding issues!
Adopting Infrastructure as Code (IaC): Infrastructure as Code (IaC) is a method for defining and managing infrastructure configurations through code. Adopting this practice ensures secure provisioning and configuration of infrastructure from the beginning.
Code Reviews and Static Analysis: Incorporate security code reviews and static analysis tools into the development process. These tools can identify security vulnerabilities in the codebase, such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms, before they make their way into the final product.
Threat Modeling: Threat modeling is an approach that helps identify potential security threats and vulnerabilities at the design stage. By analyzing the application’s architecture, data flow, and potential attack vectors, teams can make informed decisions about mitigations and safeguards early on.
Secure Development Frameworks and Libraries: The use of libraries and frameworks with built-in security features reduces the chance of introducing vulnerabilities and speeds up the development by providing tested and secure building blocks.
Automated Testing: Integrate automated security testing into the continuous integration and continuous deployment (CI/CD) pipeline. Automated security tests, including vulnerability scanning and security-focused unit tests, provide immediate feedback to developers about security issues within their code.
Container Security: To keep containers safe, it is important to secure the container images, the software that runs them, and the systems that manage them, like Kubernetes. Following the right security rules protocols stops unauthorized people from getting in and keeps the containers safe from problems, making sure the applications are protected.
In the past, both development and security teams struggled to gauge their progress and determine the necessary next steps. The DevSecOps Maturity Model was introduced to address this challenge—it is a structured framework for organizations to assess their current security practices and prioritize improvements.
This model enables organizations to understand the desired level of security, and identify areas for enhancement across various domains. It offers a clear roadmap for implementing DevSecOps practices throughout the organization, with four stages: beginner, intermediate, advanced, and expert.
Key Advantages:
Enhances overall operational efficiency
Increases the frequency of software releases
Strengthens the organization’s security stanceposture
Reduces time-to-market for new features
Improves the quality and performance of applications
Accelerates the delivery speed of updates
Provides valuable insights for continuous improvement and future growth
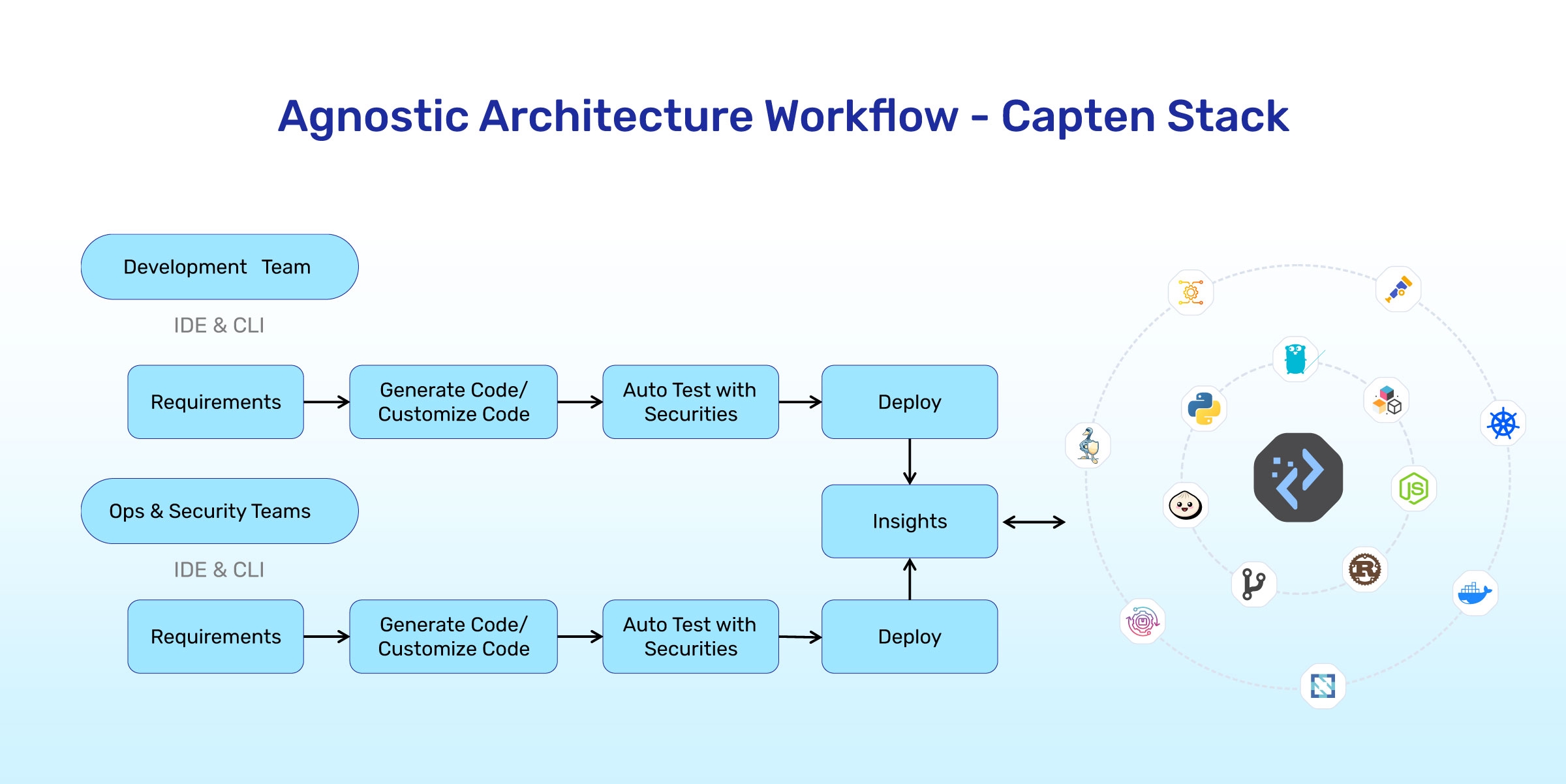
Capten Stack offers a comprehensive suite of toolsis designed to streamline and secure the software development lifecycle for organizations. This self-service platform suite helps DevSecOps teams to integrate security practices throughout the development process.
Compage: Compage (auto-code generator) simplifies the backend development process, accelerating product delivery and easing the transition to cloud-native environments. Compage enforces security policies within the software supply chain, all through an intuitive visual interface. This helps developers to focus on core functionalities while maintaining strong security.
Quality Trace: This open-source functional testing framework utilizes open telemetry for trace-based testing. Quality Trace offers in-depth insights throughout the development cycle, promoting early detection of issues and continuous improvement. This translates to a more stable and reliable application for end-users.
Opty: Opty is a dynamic optimization solution that helps Kubernetes workloads achieve peak performance and cost-efficiency. Through comprehensive analysis, Opty optimizes resource allocation for applications, simplifying the path for developers to create efficient cloud-native ecosystems.
Kubviz: This all-in-one platform provides observability for Kubernetes, Git, and container environments. Kubviz empowers operations and SRE teams to efficiently troubleshoot issues, leading to a smoother DevSecOps workflow and enhanced security posture.
Capten: This platform fosters seamless collaboration across DevSecOps teams, enabling application and infrastructure modernization, automation, and robust security measures. Capten eliminates the traditional trade-off between speed and security, allowing for secure and efficient cloud-native development.
Tarian: Leveraging advanced technologies, Tarian delivers real-time protection for cloud-native workloads within Kubernetes environments. This includes advanced anomaly detection and automated threat elimination, ensuring a constantly secure ecosystem for your applications.
Try Capten Stack today and empower your development, security and operations teams with streamlined, secure, and collaborative tools for cloud-native excellence. Optimize your workflows, enhance security, and accelerate delivery in modern IT environments. Take your operations to the next level. Get in touch today – hello@intelops.ai.

Gone are the days of monolithic applications and siloed data centres. Enterprises are increasingly adopting …
Gone are the days of simple, monolithic applications running on a centralized infrastructure. Today’s …
Digital transformation has reshaped how businesses operate, keeping customers at the forefront. Its urgency …
Finding the right talent is pain. More so, keeping up with concepts, culture, technology and tools. We all have been there. Our AI-based automated solutions helps eliminate these issues, making your teams lives easy.
Contact Us